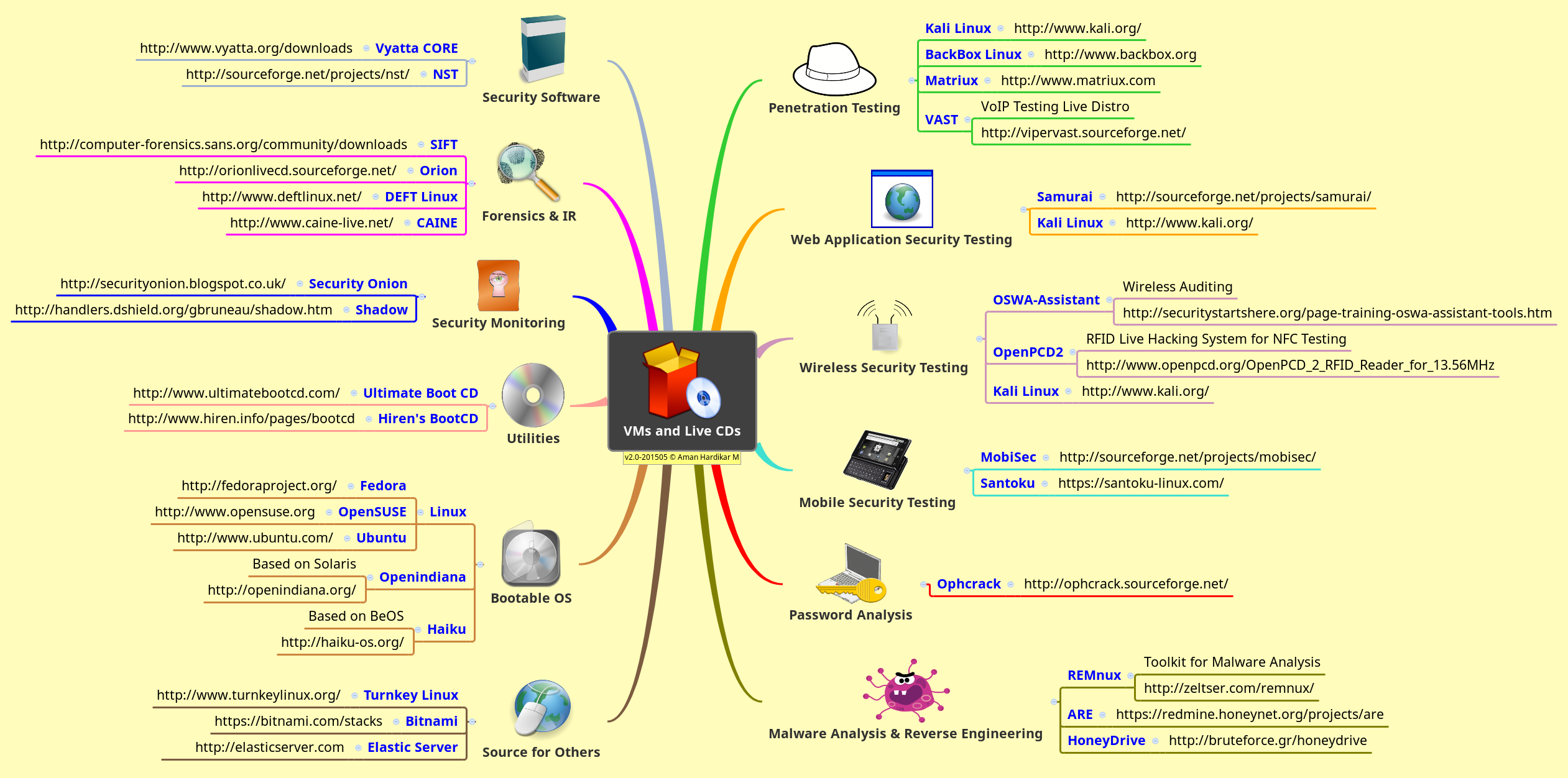
Sox Iso 27001 Mapping Satellite
An enterprise IT environment can generate millions of logs in a single day. While the vast majority are routine messages not requiring any particular action, within the group may be a handful of significant events. Determining what constitutes a meaningful event and automating the process of notifying an Satellite administrator when it occurs is a key function of an and.
But what if the threat is something that unfolds slowly, from multiple sources over an extended period? Even with automated event filtering, detailed forensic reports and real-time alerting, some behavior may be so subtle that it escapes notice by traditional log management and SIEM solutions. With the geographic and logical complexities in today’s information technology landscape, organizations are confronted with extensive challenges maintaining and operating a secure enterprise network. In response to these challenges, LogRhythm offers fully interactive network visualization and relationship mapping and combines it with fully integrated geolocation capabilities. Along with trending charts and fully interactive graphical analytics, LogRhythm provides customers with exceptional visual correlation capabilities and global event awareness. Geolocation With Geolocation, LogRhythm provides automated geographic context around any event. The source of the event can be associated with the country of origin, region, or state and the city where the event originated.
This feature adds global context to geographically distributed enterprise environments and provides administrators with greater awareness of what events are happening and where. Satellite Map LogRhythm’s geolocation capabilities also extend beyond the corporate network. With a subscription service, customers of any size can automatically receive geographic context identifying the country, region and city of any anonymous log source or destination. LogRhythm can use the additional geographic context to correlate events based on global considerations. With geolocation, administrators can be alerted immediately of events such as excessive outbound communication outside of the accepted geographic boundaries of the network. Using a simple wizard, they can quickly call up the details of all relevant outbound communication, such as where it was originated, other potentially impacted systems and applications and responsible users and/or processes.
Network Visualization LogRhythm’s Network Visualization tool allows users to map the relationships between any number of hosts from anywhere in the world, whether inside or outside the network. As an added benefit, it incorporates automated geolocation data for maximizing relevant context. Investigations on any criteria identify communication between devices and how it all ties together. Network Visualization provides a graphic representation of the communication details associated with any investigation.
Administrators use a standard, wizard-based interface to define the specifics of what they want to investigate. Network Visualization immediately displays a visual representation of communication between all associated hosts, including a breakdown of logical and physical boundaries.
In addition to where communication is taking place, Network Visualization also provides addition detail about what is being communicated. Network Visualization maps not only show the location of each associated host, but they are also capable of applying network-specific context. This includes information such as bytes in/bytes out and total log count to help identify the origin points and destinations with the highest amount of activity. Once a Network Visualization relationship map is generated, it has the same interactive capabilities as any LogRhythm tool.
Users can quickly drill down to a specific host or group of hosts, with full filter-on-the-fly capabilities. And as a fully integrated function of LogRhythm, search criteria can be saved for future use or captured in a report with a right-click command.
Company Overview Netwrix Corporation develops and offers auditing software. It operates the Netwrix Auditor Platform that focuses on audit data solutions for IT systems such as Active Directory, Exchange, File Servers, SharePoint, SQL Server, VMware, and Windows Server. The company provides security and compliance, operations management, and business continuity solutions. It caters to healthcare, educational, financial, and government sectors. Netwrix Corporation was founded in 2006 and is headquartered in Irvine, California. Jun 20 17 Netwrix Corporation announced that Grey Owl Engineering leverages Netwrix Auditor to establish control over large sets of data, address business users' requests more efficiently and enhance the quality of services provided to customers. The firm needed a solution that would provide detailed information about files, such as whether there are other versions and who created them, who deleted any missing files, who accessed a particular file and when, and so on.
Netwrix Auditor offered all the necessary functionality. In less than a year, the firm has gained the following benefits: Complete control over files and quick investigation of user issues. Netwrix Auditor enables the firm's IT team to easily track all file read attempts, modifications, moves and deletions, and to address any issues in minutes, rather than the 2–3 hours required in the past.
Efficient data governance. The pre-built file analysis reports, which list data owners, empty folders and file duplicates, simplified data governance, improved storage optimization and increased user productivity.
The reports also helped the team to identify users with excessive permissions and reduce data exposure. Improved employee behavior. To increase employee accountability, the firm's managers use the data provided by Netwrix Auditor during training on policies and procedures. As a result, employees are more careful about changing or deleting files.
May 30 17 Netwrix Corporation announced the release of Netwrix Auditor Free Community Edition. This new freeware helps small businesses and startups stay informed about what's happening across their IT infrastructures while meeting budgetary constraints. IT pros in small companies spend a lot of time poring over piles of log data trying to find out exactly what is happening in the IT environment. Built on proven Netwrix technology, the free edition of Netwrix Auditor provides visibility into changes and access events in hybrid IT environments by tracking user activity across on-premises and cloud-based systems. The key benefits of Netwrix Auditor Free Community Edition include: Automated user activity monitoring. The free edition of Netwrix Auditor tracks all changes and access events made during the last 24 hours, including the before and after values for each modification, and automatically delivers the information straight to your mailbox every single day.
This helps IT pros spot critical changes that could lead to security incidents or systems downtime, such as the altering of permissions to sensitive folders on a file server, the installation of suspicious software and so on. Netwrix Auditor Free Community Edition scales with your business and seamlessly upgrades to the full version of Netwrix Auditor, which delivers complete visibility into user behavior for data security and risk mitigation.
Sox Iso 27001 Mapping Satellites
Cost efficiency. The free edition of Netwrix Auditor provides customers with reports on user activity in their IT environments for as long as they need at no cost. Wide scope of supported systems. All systems supported in the commercial edition of Netwrix Auditor are also supported in the free edition, which eliminates the need to juggle multiple free tools that report on events in only one particular system. The list of supported systems includes Active Directory, file servers, Exchange, Windows Server, Oracle Databases, SQL Server, Office 365 and more.

May 3 17 Netwrix Corporation announced the release of Netwrix Auditor 9.0. The newest version of the platform introduces functionality that enables organizations to respond immediately to ransomware and aberrant insider activity, identify and block threats to their network infrastructures, granularly restrict access to security intelligence, and slash preparation time for audits. New capabilities available in Netwrix Auditor 9.0 include: Alerts on threat patterns. Threshold-based alerting on file server activity protects data against ransomware. In addition, this functionality enables users to stay on top of other suspicious behavior patterns and security violations across all their on-premises and cloud-based IT systems to ensure fast response to external attacks and insider threats. Users can choose from the list of predefined alerts or specify any pattern of behavior they consider risky. Add-on for Cisco.
This new free add-on, which is available in the Netwrix Auditor Add-on Store, provides pervasive visibility into the activity around network devices, which is normally minimal, so users can spot any outliers and prevent malicious actors from taking control over traffic. They can now minimize the risk of network sniffing and other nefarious attacks aimed at monitoring or manipulating the traffic to and from the network, or masking illegitimate access to critical systems. Role-based access control. Users can now establish and enforce segregation of duties as recommended by industry best practices and required by many security regulations. With fine-grained controls, organizations can easily ensure that IT and business teams have exactly the right access to security intelligence and settings. Reports aligned with GDPR, CJIS, GLBA, FERPA and NERC CIP. In addition to report packs for the common regulatory standards supported earlier, such as HIPAA, PCI DSS, SOX, FISMA/NIST and ISO/IEC 27001, Netwrix Auditor 9.0 includes new sets of out-of-the-box compliance reports mapped to the specific requirements of GDPR, CJIS, GLBA, FERPA and NERC CIP.
This broad coverage helps relieve the compliance burden and slash preparation time for audits.